_SIKUR
Critical Asset Management Aligned with Best Security Practices
TENTI, in partnership with SIKUR, offers advanced solutions to protect corporate and government data, ensuring privacy and security against cyber threats. In today’s environment, where integration of systems, equipment, and connected devices is increasingly necessary, an attack on an Operational Technology (OT) network or an Industrial Control System (ICS) device can originate from a vulnerability exploited in an Information Technology (IT) system. Centralized and integrated management of these critical assets significantly reduces the risk of cyberattacks.
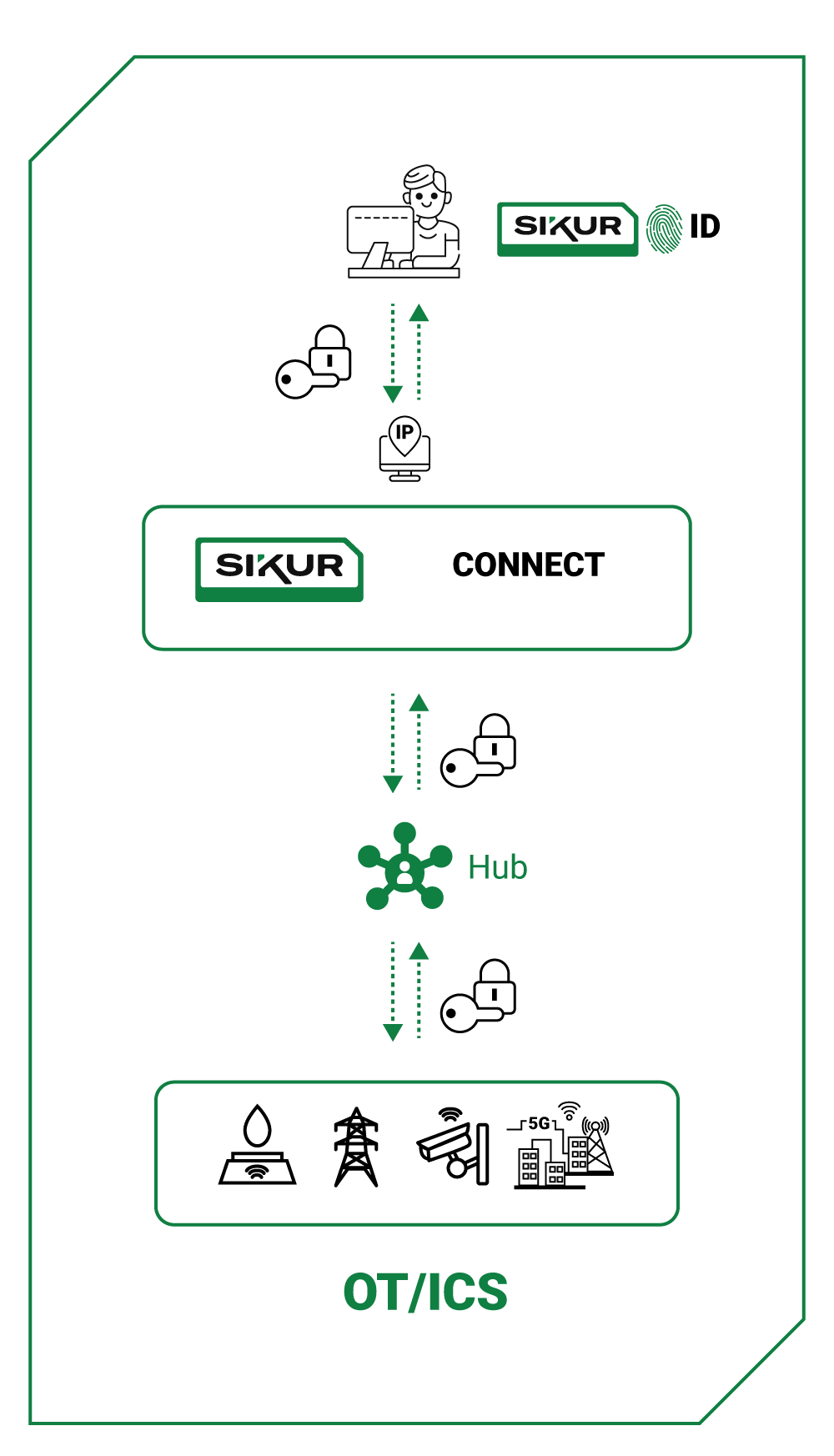
With an innovative approach, the solution enables passwordless authentication through facial or fingerprint biometrics, removing the need for vulnerable credentials and reducing the risk of fraud. Additionally, through the SIKUR Connect platform, it is possible to implement effective access management for OT and ICS systems, eliminating the need for VPNs, reducing costs, and ensuring these systems are disconnected from the public internet, enhancing their security.
Based on industry best practices, the solution complies with major international regulations such as the General Data Protection Regulation (GDPR, 2016), the U.S. IoT Cybersecurity Improvement Act (2020), and the UK Government’s Code of Practice for Consumer IoT Security (2021).
Key Features
Identity Management
Allows users to access authorized devices without needing to know credentials
Identity Management
Allows users to access authorized devices without needing to know credentials
Passwordless Authentication
Ensures secure platform access without passwords, preventing fraud
Passwordless Authentication
Ensures secure platform access without passwords, preventing fraud
Audit and Compliance
Logs records, keylogger data, and video for audits in accordance with global standards
Audit and Compliance
Logs records, keylogger data, and video for audits in accordance with global standards
Secure Data Collection and Storage
Protects and securely stores device data
Secure Data Collection and Storage
Protects and securely stores device data
Secure and Reverse Tunnel
Ensures secure access to devices via encrypted tunnels, reducing operational costs
Secure and Reverse Tunnel
Ensures secure access to devices via encrypted tunnels, reducing operational costs
Zero Touch
Simplifies remote deployment and provisioning of devices without physical contact
Zero Touch
Simplifies remote deployment and provisioning of devices without physical contact
Device Management
Ensures secure access, updates, and protection against device theft
Device Management
Ensures secure access, updates, and protection against device theft
No Default Passwords
Replaces passwords with private keys on IoT devices, aligning with security regulations
No Default Passwords
Replaces passwords with private keys on IoT devices, aligning with security regulations
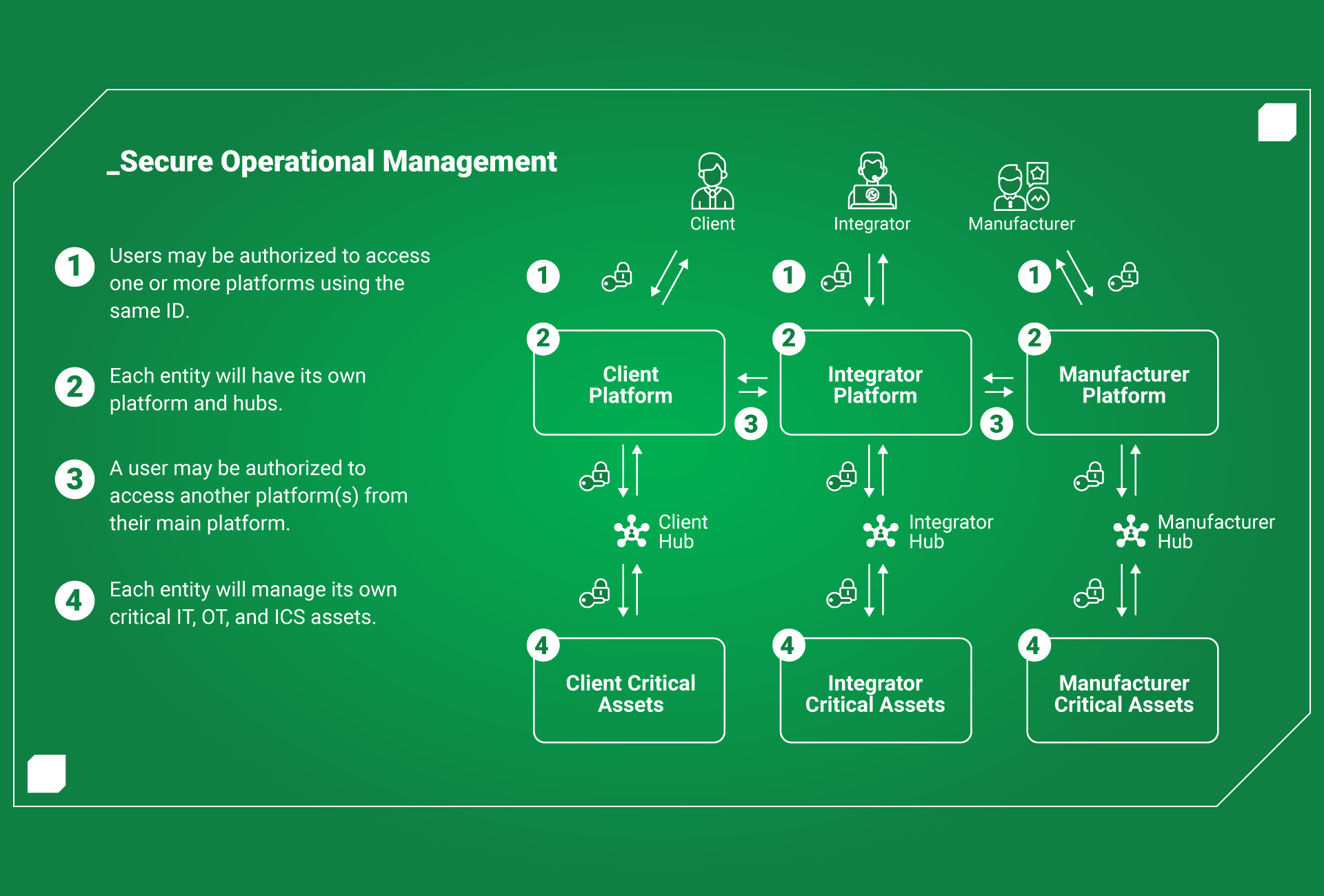
How can the solution help you?